With the prevalence of cyberattacks, it’s imperative that every company has a cybersecurity plan. Attacks are so frequent, it can be hard to keep up with the latest breaches. Troy Hunt, a Microsoft MVP & Microsoft Regional Director, created a website, Have I Been Pwned to allow users to check if their email address has been compromised while also keeping visitors updated about the latest data breaches. To date, the site currently estimates there are over 8,46,085,016 pwned accounts from over 400 websites.
To protect your company, keep your data safe (and your company off of Troy’s website), it’s important you take IT security risks seriously. Take the time to educate staff about security concerns and always stay current with software updates.
Don’t Become Complacent
Too often, people don’t take cybersecurity seriously because they don’t believe their company will be a target. While we hear about high-profile attacks on the news, businesses of all sizes are under constant threat. One of the best ways to help protect your business from IT security risks is to treat your company as a potential target for a cyberattack.
Educate Staff
Many cyberattacks are a result of human error (such as phishing scams or losing a device). To protect your company, you need to continually educate staff on proper security protocols and have policies in place to report stolen devices.
Stay On Top of Updates
Always install security updates in a timely manner. If you don’t do any other IT security risk mitigation, at least stay on top of updates. Applying critical patches and keeping to the latest version of software is one of the best defences against hackers and other types of security attacks.
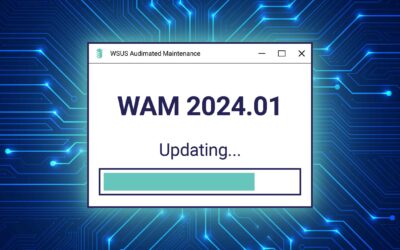
WAM is the flagship product from AJ Tek that helps system administrators automate WSUS maintenance, leaving them time to focus on more important tasks. Once installed, the software works in the background and emails a daily report for you to review. Learn how you can save time with easy WSUS cleanup.
Easily purchase WAM online and save time on WSUS maintenance.
WSUS Automated Maintenance (WAM) system was developed by AJ Tek and is used by system administrators worldwide—from Australia to Antarctica. With over 50,000 unique downloads, it’s the preferred method of WSUS maintenance worldwide.
Connect with us on Facebook and LinkedIn for additional insights and advice.